furryCTF2025赛前热身题(misc方向) 比赛网站:https://furryctf.com/games/5
1.签到题 题目描述:
1 2 3 话说,你们有发现比赛平台上藏有一个flag吗? 注意flag格式哦~
在赛题主页就可以找到:
flag为:
1 furryCTF{Hack_for_fun_not_for_profit}
2.新的一年,新的开始 题目描述:
1 2 3 4 5 6 7 8 9 10 11 Catch The Future Time to own 2025 Forever young in hacking furryCTF{h4ppY_n3w_y34r_2o25_w1th_1Ov3} 祝各位师傅: 栈上生花,堆里藏月,逆向不秃,web不坐牢,pwn穿一切,ak全场! 🚩🎉
这种就是问卷题
flag为:
1 furryCTF{h4ppY_n3w_y34r_2o25_w1th_1Ov3}
3.PassDump 1 2 3 4 5 6 7 8 9 作为CTFer,很多时候都会有电脑放一夜跑程序的经历。 但猫猫看着跑一夜碰撞之后蓝屏的电脑,陷入了沉思…… flag格式为furryCTF{出现问题的文件_蓝屏错误代码_该文件的最后一次编译时间_失败事件的缩写_当时正在使用的应用程序的名称} 例如,这是一个合法的flag: furryCTF{system.exe_0x0000001A_2024.12.31-14:00:00_DPC_Notepad}
这题需要用到windbg,这里链接就不贴了,网上一搜就有
打开windbg后
打开command,也就是命令行
一般会有这个蓝标字体,如果没有就自己输入
这里我把输出结果放一下
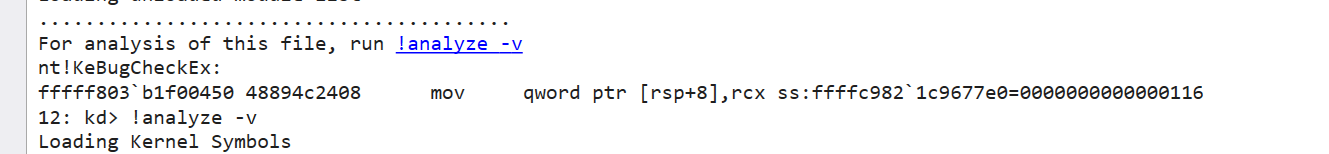
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 231 232 233 234 235 236 237 238 239 240 241 242 243 244 245 246 247 248 249 250 251 252 253 254 255 256 257 258 259 260 261 262 263 264 265 266 267 268 269 270 271 272 273 274 275 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 12: kd> !analyze -v Loading Kernel Symbols .. Press ctrl-c (cdb, kd, ntsd) or ctrl-break (windbg) to abort symbol loads that take too long. Run !sym noisy before .reload to track down problems loading symbols. ............................................................. ................................................................ ................................................................ ................................................................ .............................................. Loading User Symbols Loading unloaded module list ......................................... ******************************************************************************* * * * Bugcheck Analysis * * * ******************************************************************************* VIDEO_TDR_FAILURE (116) Attempt to reset the display driver and recover from timeout failed. Arguments: Arg1: ffffe30a4b8cd010, Optional pointer to internal TDR recovery context (TDR_RECOVERY_CONTEXT). Arg2: fffff8035ce14790, The pointer into responsible device driver module (e.g. owner tag). Arg3: ffffffffc000009a, Optional error code (NTSTATUS) of the last failed operation. Arg4: 0000000000000004, Optional internal context dependent data. Debugging Details: ------------------ Unable to load image nvlddmkm.sys, Win32 error 0n2 *** WARNING: Unable to verify timestamp for nvlddmkm.sys KEY_VALUES_STRING: 1 Key : Analysis.CPU.mSec Value: 2140 Key : Analysis.Elapsed.mSec Value: 13194 Key : Analysis.IO.Other.Mb Value: 0 Key : Analysis.IO.Read.Mb Value: 1 Key : Analysis.IO.Write.Mb Value: 0 Key : Analysis.Init.CPU.mSec Value: 484 Key : Analysis.Init.Elapsed.mSec Value: 28118 Key : Analysis.Memory.CommitPeak.Mb Value: 102 Key : Analysis.Version.DbgEng Value: 10.0.29482.1003 Key : Analysis.Version.Description Value: 10.2509.29.03 amd64fre Key : Analysis.Version.Ext Value: 1.2509.29.3 Key : Bugcheck.Code.LegacyAPI Value: 0x116 Key : Bugcheck.Code.TargetModel Value: 0x116 Key : Dump.Attributes.AsUlong Value: 0x21808 Key : Dump.Attributes.DiagDataWrittenToHeader Value: 1 Key : Dump.Attributes.ErrorCode Value: 0x0 Key : Dump.Attributes.KernelGeneratedTriageDump Value: 1 Key : Dump.Attributes.LastLine Value: Dump completed successfully. Key : Dump.Attributes.ProgressPercentage Value: 0 Key : Failure.Bucket Value: 0x116_IMAGE_nvlddmkm.sys Key : Failure.Exception.IP.Address Value: 0xfffff8035ce14790 Key : Failure.Exception.IP.Module Value: nvlddmkm Key : Failure.Exception.IP.Offset Value: 0x1854790 Key : Failure.Hash Value: {c89bfe8c-ed39-f658-ef27-f2898997fdbd} Key : Faulting.IP.Type Value: Paged Key : Hypervisor.Enlightenments.ValueHex Value: 0x7417df84 Key : Hypervisor.Flags.AnyHypervisorPresent Value: 1 Key : Hypervisor.Flags.ApicEnlightened Value: 0 Key : Hypervisor.Flags.ApicVirtualizationAvailable Value: 1 Key : Hypervisor.Flags.AsyncMemoryHint Value: 0 Key : Hypervisor.Flags.CoreSchedulerRequested Value: 0 Key : Hypervisor.Flags.CpuManager Value: 1 Key : Hypervisor.Flags.DeprecateAutoEoi Value: 1 Key : Hypervisor.Flags.DynamicCpuDisabled Value: 1 Key : Hypervisor.Flags.Epf Value: 0 Key : Hypervisor.Flags.ExtendedProcessorMasks Value: 1 Key : Hypervisor.Flags.HardwareMbecAvailable Value: 1 Key : Hypervisor.Flags.MaxBankNumber Value: 0 Key : Hypervisor.Flags.MemoryZeroingControl Value: 0 Key : Hypervisor.Flags.NoExtendedRangeFlush Value: 0 Key : Hypervisor.Flags.NoNonArchCoreSharing Value: 1 Key : Hypervisor.Flags.Phase0InitDone Value: 1 Key : Hypervisor.Flags.PowerSchedulerQos Value: 0 Key : Hypervisor.Flags.RootScheduler Value: 0 Key : Hypervisor.Flags.SynicAvailable Value: 1 Key : Hypervisor.Flags.UseQpcBias Value: 0 Key : Hypervisor.Flags.Value Value: 55185662 Key : Hypervisor.Flags.ValueHex Value: 0x34a10fe Key : Hypervisor.Flags.VpAssistPage Value: 1 Key : Hypervisor.Flags.VsmAvailable Value: 1 Key : Hypervisor.RootFlags.AccessStats Value: 1 Key : Hypervisor.RootFlags.CrashdumpEnlightened Value: 1 Key : Hypervisor.RootFlags.CreateVirtualProcessor Value: 1 Key : Hypervisor.RootFlags.DisableHyperthreading Value: 0 Key : Hypervisor.RootFlags.HostTimelineSync Value: 1 Key : Hypervisor.RootFlags.HypervisorDebuggingEnabled Value: 0 Key : Hypervisor.RootFlags.IsHyperV Value: 1 Key : Hypervisor.RootFlags.LivedumpEnlightened Value: 1 Key : Hypervisor.RootFlags.MapDeviceInterrupt Value: 1 Key : Hypervisor.RootFlags.MceEnlightened Value: 1 Key : Hypervisor.RootFlags.Nested Value: 0 Key : Hypervisor.RootFlags.StartLogicalProcessor Value: 1 Key : Hypervisor.RootFlags.Value Value: 1015 Key : Hypervisor.RootFlags.ValueHex Value: 0x3f7 Key : WER.System.BIOSRevision Value: 1.23.0.0 BUGCHECK_CODE: 116 BUGCHECK_P1: ffffe30a4b8cd010 BUGCHECK_P2: fffff8035ce14790 BUGCHECK_P3: ffffffffc000009a BUGCHECK_P4: 4 FILE_IN_CAB: furryCTF.dmp DUMP_FILE_ATTRIBUTES: 0x21808 Kernel Generated Triage Dump FAULTING_THREAD: ffffe30a86af3040 VIDEO_TDR_CONTEXT: dt dxgkrnl!_TDR_RECOVERY_CONTEXT ffffe30a4b8cd010 Symbol dxgkrnl!_TDR_RECOVERY_CONTEXT not found. PROCESS_OBJECT: 0000000000000004 BLACKBOXACPI: 1 (!blackboxacpi) BLACKBOXBSD: 1 (!blackboxbsd) BLACKBOXNTFS: 1 (!blackboxntfs) BLACKBOXPNP: 1 (!blackboxpnp) BLACKBOXWINLOGON: 1 (!blackboxwinlogon) PROCESS_NAME: System IP_IN_PAGED_CODE: nvlddmkm+1854790 fffff803`5ce14790 488b05b9f28dff mov rax,qword ptr [nvlddmkm+0x1133a50 (fffff803`5c6f3a50)] STACK_TEXT: ffffc982`1c9677d8 fffff803`43a2375d : 00000000`00000116 ffffe30a`4b8cd010 fffff803`5ce14790 ffffffff`c000009a : nt!KeBugCheckEx ffffc982`1c9677e0 fffff803`43c97be6 : fffff803`5ce14790 ffffe30a`5b80b5a0 00000000`00000004 ffffe30a`4b8cd010 : dxgkrnl!TdrBugcheckOnTimeout+0x101 ffffc982`1c967820 fffff803`43a324be : 00000000`00000000 00000000`00002000 00000000`00000004 00000000`00000004 : dxgkrnl!ADAPTER_RENDER::Reset+0x232 ffffc982`1c967850 fffff803`43a69375 : ffffe30a`00000100 00000000`00000000 ffffc982`00000000 00000000`00000000 : dxgkrnl!DXGADAPTER::Reset+0x59a ffffc982`1c9678e0 fffff803`43a694d2 : fffff803`b290ce60 00000000`00000000 ffffb881`c42d1100 fffff803`b29cfbc0 : dxgkrnl!TdrResetFromTimeout+0x15 ffffc982`1c967910 fffff803`b1c3072c : ffffe30a`86af3040 ffffe30a`478ddae0 ffffe30a`478dda00 fffff803`44b52750 : dxgkrnl!TdrResetFromTimeoutWorkItem+0x22 ffffc982`1c967950 fffff803`b1ea007a : ffffe30a`86af3040 ffffe30a`86af3040 fffff803`b1c30140 ffffe30a`478ddae0 : nt!ExpWorkerThread+0x5ec ffffc982`1c967b30 fffff803`b20a5db4 : ffffb881`c42d1180 ffffe30a`86af3040 fffff803`b1ea0020 00000000`0e5f57dc : nt!PspSystemThreadStartup+0x5a ffffc982`1c967b80 00000000`00000000 : ffffc982`1c968000 ffffc982`1c961000 00000000`00000000 00000000`00000000 : nt!KiStartSystemThread+0x34 SYMBOL_NAME: nvlddmkm+1854790 MODULE_NAME: nvlddmkm IMAGE_NAME: nvlddmkm.sys STACK_COMMAND: .process /r /p 0xffffe30a476cb040; .thread 0xffffe30a86af3040 ; kb FAILURE_BUCKET_ID: 0x116_IMAGE_nvlddmkm.sys OSPLATFORM_TYPE: x64 OSNAME: Windows 10 FAILURE_ID_HASH: {c89bfe8c-ed39-f658-ef27-f2898997fdbd} Followup: MachineOwner ---------
对比furryCTF{system.exe_0x0000001A_2024.12.31-14:00:00_DPC_Notepad}这个格式
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 出现问题的文件:IMAGE_NAME: nvlddmkm.sys 蓝屏错误代码: VIDEO_TDR_FAILURE (116) <--- 括号里的 116 就是十进制代码 ... BUGCHECK_CODE: 116 <--- 这里确认 提取结果: 116 (十进制) = 0x00000116 (十六进制) 该文件的最后一次编译时间:lm v m nvlddmkm指令输入后运行 Browse all global symbols functions data Symbol Reload Timestamp: Tue Feb 11 13:40:16 2025 (67AAE2C0) <--- 就在这一行 CheckSum: 05B57FA7 失败事件的缩写: ******************************************************************************* * Bugcheck Analysis * ******************************************************************************* VIDEO_TDR_FAILURE (116) <--- 这里是全名 这里用TDR 当时正在使用的应用程序的名称:这里有点坑,需要一点阅读理解,“当前正在使用”,根据题目场景,当前正在进行碰撞,碰撞会想到啥,hash碰撞吧,想想常用的工具,hashcat就是答案
最后整合一下,flag为:
1 furryCTF{nvlddmkm.sys_0x00000116_2025.02.11-13:40:16_TDR_hashcat}
4.IIS服务器 题目描述:
1 2 3 猫猫前段时间闲着没事搭建了一个IIS服务器。 不过,最近猫猫发现,服务器上好像多了个文件……?
用wireshark打开pcap文件
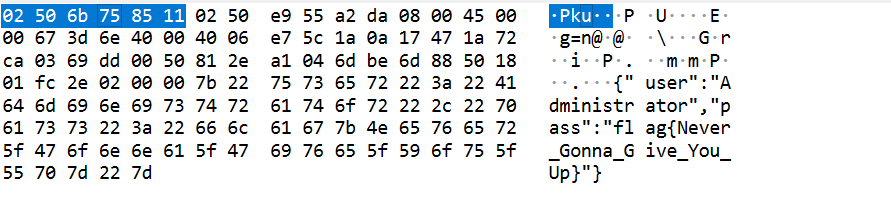
依旧先ctrl+f搜索flag,找到了交了但是是错的因为那只是一个人登录用的password
确实被骗到了哈哈哈,诈骗的小曲
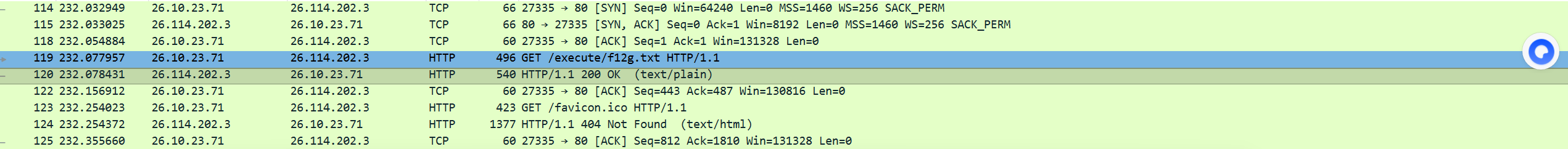
你观察就可以发现,流量大多数是TCP和http流,所以右键追踪流
最后找到一个传了fl2g.txt的流量
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 GET /execute/f12g.txt HTTP/1.1 Host: 26.114.202.3 Connection: keep-alive Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 0.000474s HTTP/1.1 200 OK Content-Type: text/plain Content-Encoding: gzip Last-Modified: Wed, 10 Jul 2024 03:14:49 GMT Accept-Ranges: bytes ETag: "c0c41d5377d2da1:0" Vary: Accept-Encoding Server: Microsoft-IIS/7.5 X-Powered-By: ASP.NET Date: Wed, 10 Jul 2024 04:37:33 GMT Content-Length: 191 0.000000s ZnVycnlDVEZ7RGlkX1lvdV9Ob3RlX1RoZV9EaWZmX0luX0Vycm9yX1BhZ2U/fQ== 0.175592s GET /favicon.ico HTTP/1.1 Host: 26.114.202.3 Connection: keep-alive User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36 Accept: image/avif,image/webp,image/apng,image/*,*/*;q=0.8 Referer: http://26.114.202.3/execute/f12g.txt Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 0.000349s HTTP/1.1 404 Not Found Content-Type: text/html Server: Microsoft-IIS/7.5 X-Powered-By: ASP.NET Date: Wed, 10 Jul 2024 04:37:34 GMT Content-Length: 1163 0.000000s <!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Strict//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-strict.dtd"> <html xmlns="http://www.w3.org/1999/xhtml"> <head> <meta http-equiv="Content-Type" content="text/html; charset=gb2312"/> <title>404 - ..................</title> <style type="text/css"> <!-- body{margin:0;font-size:.7em;font-family:Verdana, Arial, Helvetica, sans-serif;background:#EEEEEE;} fieldset{padding:0 15px 10px 15px;} h1{font-size:2.4em;margin:0;color:#FFF;} h2{font-size:1.7em;margin:0;color:#CC0000;} h3{font-size:1.2em;margin:10px 0 0 0;color:#000000;} #header{width:96%;margin:0 0 0 0;padding:6px 2% 6px 2%;font-family:"trebuchet MS", Verdana, sans-serif;color:#FFF; background-color:#555555;} #content{margin:0 0 0 2%;position:relative;} .content-container{background:#FFF;width:96%;margin-top:8px;padding:10px;position:relative;} --> </style> </head> <body> <div id="header"><h1>..........</h1></div> <div id="content"> <div class="content-container"><fieldset> <h2>404 - ..................</h2> <h3>......................................................</h3> </fieldset></div> </div> </body> </html>
这个是不是很像base64啊,虽然不是Zmxh这种标准开头
1 2 0.000000s ZnVycnlDVEZ7RGlkX1lvdV9Ob3RlX1RoZV9EaWZmX0luX0Vycm9yX1BhZ2U/fQ==
解密之后得到flag(这里用随波逐流)
1 furryCTF{Did_You_Note_The_Diff_In_Error_Page?}
5.盲盒 题目描述:
1 2 3 4 5 来开盲盒吧~nwn 注:本题原本的flag格式为flag{},因为懒得改附件了,所以找到flag后请将里面的“flag”修改为“furryCTF” 比如flag{Hi}修改为furryCTF{Hi}即为正确答案。
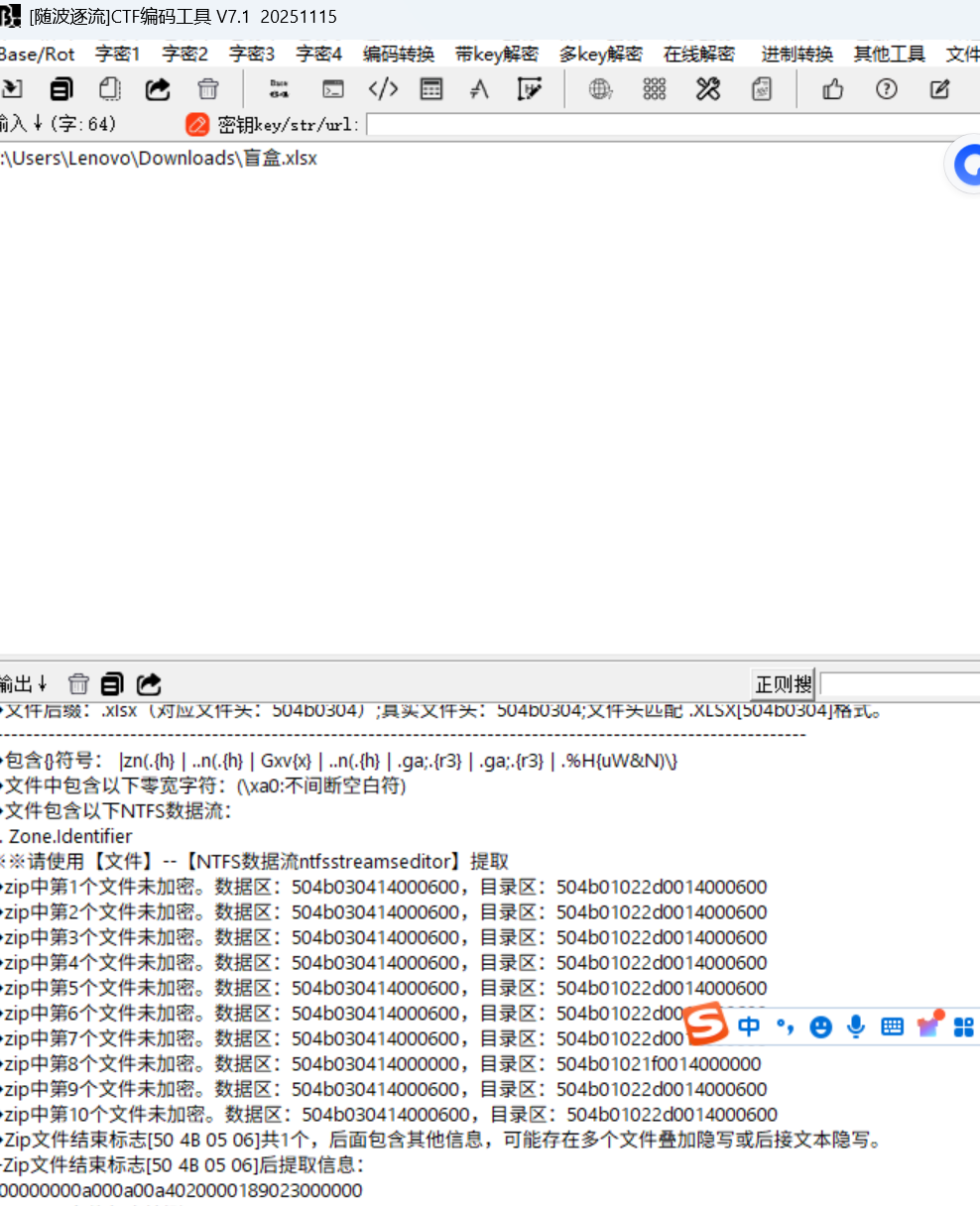
像这种word,excel,ppt这种题目,这种隐写的一般的处理方式就是把文件当压缩包去看
直接用随波逐流的binwalk工具去分离
一个一个文件找啊找,看有没有和flag相关的
在sharedStrings里
1 2 3 <?xml version="1.0" encoding="UTF-8" standalone="yes"?> <sst xmlns="http://schemas.openxmlformats.org/spreadsheetml/2006/main" count="762826" uniqueCount="2"><si><t>来开盲盒吧~</t><phoneticPr fontId="1" type="noConversion"/></si><si><t>flag 不在这</t><phoneticPr fontId="1" type="noConversion"/></si></sst> <!-- 我也没说flag在这呀nwn,你不会想在这里找到flag叭~ -->
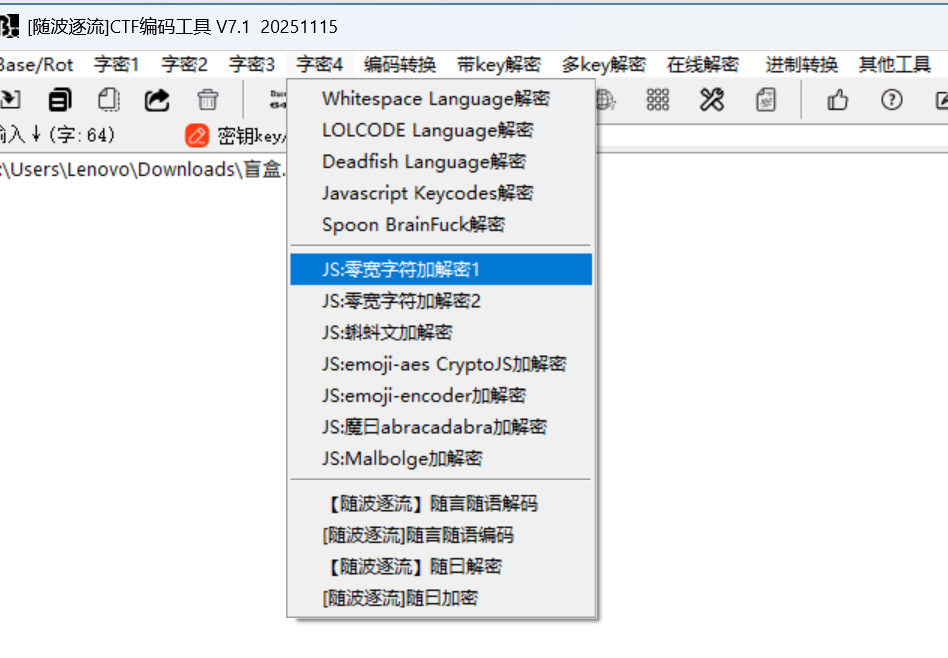
是不是很明显的零宽隐写
到网站里,随波逐流的就可以
然后你就看到flag了
flag为:
1 flag{Z19_The_Str1ng_In_Exc9l}